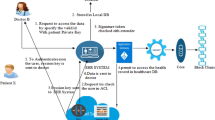
Abstract
In the cloud computing, different cloud service providers are often in different trust domains. As the traditional identity authentication mode cannot be applied to the cloud computing, the cross-domain identity authentication mechanism is needed to solve the identity authentication problem in the cloud computing. In view of the security problems in cloud computing, a cross-domain identity authentication scheme based on group signature is proposed. This scheme introduces a group of cloud service providers and users who are located in different trust domains. Any member of the group can generate the signature on behalf of the whole group, making the user access the cloud service provider in the case of privacy security. At the same time, with traceability it can track illegal operation of illegal users. In addition, the scheme uses the Chinese Remainder Theorem to integrate the message, and it can control the length of the data in the calculation process, simplifying the calculation process. It also realizes the join and revocation of group members without changing the key of other legitimate group members, and the maintenance cost of authentication schemes is low. The results show that the scheme has the advantages of anonymity, anti-counterfeit, traceability, anti- joint attack and so on. It can not only realize tracking function under the condition of guaranteeing user’s privacy, but can also simplify the authentication calculation process to improve the efficiency of the cross domain identity authentication, and its performance is more suitable for large-scale cloud computing environment.
Similar content being viewed by others
References
Feng Z S, Qin Z G, Yuan D, et al. Key techniques of access control for cloud computing[J]. Acta Electronica Sinica, 2015, 43 (2): 312–319(Ch).
Wang Q, Li F J, Qin Y Y. An identity authentication model for cloud computing[J]. Application of Electronic Technique, 2015, 41 (2): 135–138(Ch).
Wang Z H, Han Z, Liu J Q, et al. ID authentication scheme based on PTPM and certificateless public key cryptography in cloud environment[J]. Journal of Software, 2016, 27 (6): 1523–1537(Ch).
Lin C, Su W B, Meng K, et al. Cloud computing security: Architecture, mechanism and modeling[J]. Chinese Journal of Computers, 2013, 36 (9): 1765–1784(Ch).
Castiglione A, Palmieri F, Chen C L, et al. A blind signature–based approach for cross–domain authentication in the cloud environment[J]. International Journal of Data Warehousing & Mining, 2017, 12(1): 34–48.
Tbatou Z, Asimi A, Asimi Y, et al. A new mutuel kerberos authentication protocol for distributed systems[J]. International Journal of Network Security, 2017, 19(6): 889–898.
Ran C, Shahaf D, Vald M. Universally composable authentication and key–exchange with global PKI[C]// IACR International Workshop on Public Key Cryptography. Berlin, Heidelberg: Springer–Verlag, 2016: 265–296.
Binu S, Misbahuddin M, Raj P. A mobile based remote user authentication scheme without verifier table for cloud based services[C]// International Symposium on Women in Computing and Informatics. New York: ACM, 2015: 502–509.
Tian J F, Sun K H. Trust–distributed–based authentication mechanism using hierarchical identity–based cryptography[J]. Journal of Computer Research and Development, 2015, 52(7): 1660–1671(Ch).
Amin R, Islam S K H, Biswas G P, et al. Design of anonymity preserving three–factor authenticated key exchange protocol for wireless sensor network[J]. Computer Networks, 2016, 101(C): 42–62.
Kleedorfer F, Panchenko Y, Busch C M, et al. Verifiability and traceability in a linked data based messaging system[C]// International Conference on Semantic Systems. New York: ACM, 2016: 97–100.
Luo C Y, Huo S W, Xin H Z. Identity–Based inter–domain authentication scheme in pervasive computing environments[ J]. Journal on Communications, 2011, 32(9): 111–115(Ch).
Brindha M, Gounden N A. A chaos based image encryption and lossless compression algorithm using hash table and Chinese Remainder Theorem[J]. Applied Soft Computing, 2016, 40: 379–390.
Cheng X G, Wang J, Du J X. Survey on group signature[J]. Application Research of Computers, 2013, 30 (10): 2881–2886(Ch).
Mishra R. Anonymous remote user authentication and key agreement for cloud computing[C]// Proceedings of the Third International Conference on Soft Computing for Problem Solving. Berlin: Springer–Verlag, 2014: 899–913.
Dong Z, Zhang L, Li J. Security enhanced anonymous remote user authentication and key agreement for cloud computing[ C]// International Conference on Computational Science and Engineering. Washington D C: IEEE, 2015: 1746–1751.
Li S B, Fu J M, Zhang H G, et al. Scheme on user identity attribute preserving based on ring signcryption for cloud computing [J]. Journal on Communications, 2014, 35 (9): 99–111(Ch).
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: Supported by the National Natural Science Foundation of China(U1304614, U1204703), the Construct Program of the Key Discipline in Zhengzhou Normal University. Aid Program for Science and Technology Innovative Research Team of Zhengzhou Normal University, Henan Province Education Science Plan General Topic ((2018)-JKGHYB-0279)
Rights and permissions
About this article
Cite this article
Yang, Y., Hu, M., Kong, S. et al. Scheme on Cross-Domain Identity Authentication Based on Group Signature for Cloud Computing. Wuhan Univ. J. Nat. Sci. 24, 134–140 (2019). https://doi.org/10.1007/s11859-019-1378-6
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11859-019-1378-6
Key words
- cloud computing
- cross-domain identity authentication
- group signature
- Chinese Remainder Theorem
- traceability