Abstract
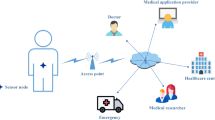
Recent advances in medical treatment and emergency applications, the need of integrating wireless body area network (WBAN) with cloud computing can be motivated by providing useful and real time information about patients’ health state to the doctors and emergency staffs. WBAN is a set of body sensors carried by the patient to collect and transmit numerous health items to medical clouds via wireless and public communication channels. Therefore, a cloud-assisted WBAN facilitates response in case of emergency which can save patients’ lives. Since the patient’s data is sensitive and private, it is important to provide strong security and protection on the patient’s medical data over public and insecure communication channels. In this paper, we address the challenge of participant authentication in mobile emergency medical care systems for patients supervision and propose a secure cloud-assisted architecture for accessing and monitoring health items collected by WBAN. For ensuring a high level of security and providing a mutual authentication property, chaotic maps based authentication and key agreement mechanisms are designed according to the concept of Diffie-Hellman key exchange, which depends on the CMBDLP and CMBDHP problems. Security and performance analyses show how the proposed system guaranteed the patient privacy and the system confidentiality of sensitive medical data while preserving the low computation property in medical treatment and remote medical monitoring.




Similar content being viewed by others
References
Ali, A., and Khan, F.A., Key agreement schemes in wireless body area networks: taxonomy and state-of-the-art. J. Med. Syst. 39:115, 2015.
Bergamo, P., Arco, P., Santis, A., Kocarev, L., Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Transactions on Circuits and Systems I 52(7):1382–1393, 2005.
Canetti, R., and Krawczyk, H., Analysis of key-exchange protocols and their use for building secure channels. Lect. Notes Comput. Sci. 2045:453–474, 2001.
Chen, C.L., Yang, T.T., Shih, T.F., A secure medical data exchange protocol based on cloud environments. J. Med. Syst. 38:112, 2014.
Fortino, G., Guerrieri, A., Giannantonio, R., Bellifemine, F.: SPINE2: developing BSN applications on heterogeneous sensor nodes. In: Proceedings of IEEE Symposium on Industrial Embedded Systems (SIES 2009), pp. 8–10. Special Session on Wireless Health, Lausanne (2009)
Fortino, G., Pathan, M., DiFatta, G.: BodyCloud: integration of cloud computing and body sensor networks. In: Proceedings of IEEE 4th International Conference on Cloud Computing Technology and Science (CloudCom 2012), pp. 3–6, Taipei (2012)
Fortino, G., and Pathan, M., Integration of Cloud computing and body sensor networks. Futur. Gener. Comput. Syst. 35:57–61, 2014.
Guo, P., Wang, J., Li, B., Lee, S., A variable threshold-value authentication architecture for wireless mesh networks. J. Internet Technol. 15(6):929–936, 2014.
Habetha, J.: The myheart project - fighting cardiovascular diseases by prevention and early diagnosis. In: Proceedings of 28th IEEE Annual International Conference on Engineering in Medicine and Biology Society (EMBS 2006), pp. 6746–6749, New York (2006)
HAVO: http://www.hvc.com.tw/lang/HAVO-E/Home%20HAVO.html, Available access: 2015/04/18
He, D., Kumar, N., Chilamkurti, N., A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 321:263–277, 2015.
He, D., and Zeadally, S., Authentication protocol for ambient assisted living system. IEEE Commun. Mag. 35(1):71–77, 2015.
He, D., Kumar, N., Chen, J., Robust anonymous authentication protocol for healthcare applications using wireless medical sensor networks. Multimedia Systems 21(1):49–60, 2015.
He, D., and Wang, D., Robust biometrics-based authentication scheme for multi-server environment. IEEE Syst. J. 9(3):816–823, 2015.
Jabbari, A., and Bagherzadeh, J., A revised key agreement protocol based on chaotic maps. Nonlinear Dyn. 78(1):669–680, 2014.
Jiang, Q., Ma, J., Ma, Z., Li, G., A privacy enhanced authentication scheme for telecare medical information systems. J. Med. Syst. 37:9897, 2013.
Khan, F.A., Ali, A., Abbas, H., Haldar, N.A.H., A cloud-based healthcare framework for security and patients’ data privacy using wireless body area networks. Procedia Comput. Sci. 34:511–517, 2014.
Li, C.T., Lee, C.C., Weng, C.Y., An extended chaotic maps based user authentication and privacy preserving scheme against DoS attacks in pervasive and ubiquitous computing environments. Nonlinear Dyn. 74(4): 1133–1143, 2013.
Li, C.T., Lee, C.C., Weng, C.Y., A secure chaotic maps and smart cards based password authentication and key agreement scheme with user anonymity for telecare medicine information systems. J. Med. Syst. 38(9):1–11, 2014.
Li, C.T., Lee, C.W., Shen, J.J., An extended chaotic maps based keyword search scheme over encrypted data resist outside and inside keyword guessing attacks in cloud storage services. Nonlinear Dyn. 80(3):1601–1611, 2015.
Li, C.T., Lee, C.C., Weng, C.Y., A dynamic identity-based user authentication scheme for remote login systems. Security and Communication Networks 8(18):3372–3382, 2015.
Li, C.T., Lee, C.C., Weng, C.Y., Fan, C.I., A secure dynamic identity based authentication protocol with smart cards for multi-server architecture. J. Inf. Sci. Eng. 31(6):1975–1992, 2015.
Li, C.T., Weng, C.Y., Lee, C.C., A secure RFID tag authentication protocol with privacy preserving in telecare medicine information systems. J. Med. Syst. 39(8):1–8, 2015.
Li, C.T., Weng, C.Y., Lee, C.C., Wang, C.C., A hash based remote user authentication and authenticated key agreement scheme for the integrated EPR information system. J. Med. Syst. 39(11):1–11, 2015.
Li, C.T., Lee, C.C., Wang, C.C., Yang, T.H., Chen, S.J., Design flaws in a secure medical data exchange protocol based on cloud environments. Lect. Notes Comput. Sci. 9532, 2015.
Li, C. T., Lee, C. C., Weng, C. Y., A chaotic maps based key agreement and user anonymity protocol without using smart cards and symmetric key en/decryptions. J. Internet Technol., 2015. article in press.
Liu, J., Zhang, Z., Chen, X., Kwak, K., Certificateless remote anonymous authentication schemes for wireless body sensor networks. IEEE Transactions on Parallel and Distributed Systems 25(2):332–342, 2014.
Lounis, A., Hadjidj, A., Bouabdallah, A., Challal, Y., Healing on the cloud: Secure cloud architecture for medical wireless sensor networks. Futur. Gener. Comput. Syst., 2015. article in press.
Mana, M., Feham, M., Bensaber, B.A., Trust key management scheme for wireless body area networks. Int. J. Netw. Security 12(2):75–83, 2011.
Muhammad, K.R.R.S., Lee, H., Lee, S., Lee, Y.K., BARI+: a biometric based distributed key management approach for wireless body area networks. Sensors 10(4):3911–3933, 2010.
Nadeem, A., Hussain, M.A., Owais, O., Salam, A., Iqbal, S., Ahsan, K., Application specific study, analysis and classification of body area wireless sensor network applications. Comput. Netw. 83:363–380, 2015.
Pacelli, M., Loriga, G., Taccini, N., Paradiso, R.: Sensing fabrics for monitoring physiological and biomechanical variables: E-textile solutions. In: 3rd IEEE/EMBS International Summer School on Medical Devices and Biosensors, pp. 1–4, Cambridge (2006)
Ren, Y., Pazzi, R.W.N., Boukerche, A., Monitoring patients via a secure and mobile healthcare system. IEEE Wirel. Commun. 17(1):59–65, 2010.
Ren, Y., Shen, J., Wang, J., Han, J., Lee, S., Mutual verifiable provable data auditing in public cloud storage. J. Internet Technol. 16(2):317–324, 2015.
RFC 2104 - HMAC: Keyed-hashing for message authentication. <http://www.ietf.org/rfc/rfc2104.txt >
Saleem, S., Ullah, S., Kwak, K.S., A study of IEEE 802.15.4 security framework for wireless body area networks. Sensors 11(2):1383–1395, 2011.
Shen, J., Moh, S., Chung, I.: A novel key management protocol in body area networks. In: Proceedings of the Seventh International Conference on Networking and Services (ICNS 2011), pp. 246–251, Venice (2011)
Shen, J., Tan, H., Wang, J., Lee, S., A novel routing protocol providing good transmission reliability in underwater sensor networks. J. Internet Technol. 16(1):171–178, 2015.
Subashini, S., and Kavitha, V., A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 34(1):1–11, 2011.
Wang, C., and Zhang, Y., New authentication scheme for wireless body area networks using the bilinear pairing. J. Med. Syst. 39:136, 2015.
Wu, Z.Y., Lee, Y.C., Lai, F., Lee, H.C., Chung, Y., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012.
Xia, Z., Wang, X., Sun, X., Wang, Q., A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Transactions on Parallel and Distributed Systems 27(2):340–352, 2016.
Xie, Q., Zhao, J., Yu, X., Chaotic maps-based three-party password-authenticated key agreement scheme. Nonlinear Dyn. 74(4):1021–1027, 2013.
Zhang, L., Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons & Fractals 37(3):669–674, 2008.
Zhao, Z., An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 38(2):1–7, 2014.
Zhou, J., Cao, Z., Dong, X.: BDK: secure and efficient biometric based deterministic key agreement in wireless body area networks. In: Proceedings of 8th International Conference on Body Area Networks (BodyNets 2013), Boston (2013)
Zhou, J., Cao, Z., Dong, X., Xiong, N., Vasilakos, A.V., 4S: A secure and privacy-preserving key management scheme for cloud-assisted wireless body area network in m-healthcare social networks. Inf. Sci. 314: 255–276, 2015.
Zissis, D., and Lekkas, D., Addressing cloud computing security issues. Futur. Gener. Comput. Syst. 28(3): 583–592, 2012.
Acknowledgments
The authors would like to thank the anonymous reviewers for their valuable suggestions and comments. This research was partially supported by the National Science Council, Taiwan, R.O.C.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Mobile Systems
Rights and permissions
About this article
Cite this article
Li, CT., Lee, CC. & Weng, CY. A Secure Cloud-Assisted Wireless Body Area Network in Mobile Emergency Medical Care System. J Med Syst 40, 117 (2016). https://doi.org/10.1007/s10916-016-0474-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-016-0474-9