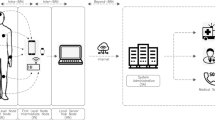
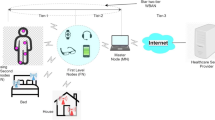
Abstract
Advances in wearable and implantable biosensors have enabled the applicability and usability of wireless body area networks (WBANs). A WBAN allows biosensors to collect and communicate human physiological data using wireless communication. The communication security of the collected data in WBAN is a major concern. Because of the dependability of cryptographic schemes for key management, these have become an important aspect of this security. However, the extremely constrained nature of biosensors has made designing key management schemes a challenging task. For this reason, many lightweight key management schemes have been proposed to overcome these constraints. In this article, we present a review of the state of the art of these solutions. We classify the WBAN schemes into three classes and evaluate them based on adequate metrics for key management in WBAN.




Similar content being viewed by others
References
Paradiso, R., Loriga, G., and Taccini, N., A wearable health care system based on knitted integrated sensors. IEEE Trans. Info. Technol. Biomed 9(3):337–344, 2005.
Djenouri, D., Khelladi, L., and Badache, N., A survey of security issues in mobile ad hoc and sensor networks. IEEE Commun. Surv. Tutorials 7(4):2–28, 2005.
Wang, Y., Attebury, G., and Ramamurthy, B., A survey of security issues in wireless sensor networks. IEEE Commun. Surv. Tutorials 8(2):2–23, 2006.
Perrig, A., Szewczyk, R., Tygar, J. D., Wen, V., and Culler, D., SPINS: Security protocol for sensor networks. Wirel. Netw 8(5):521–534, 2002.
Eschenauer, L. and Gligor, V. D., A key-management scheme for distributed sensor networks. Proc. of the Ninth Conference on Computer and Communications Security (CCS’02). ACM, Washington DC, USA, 41–47, 2002.
Zhu, S., Setia, S., and Jajodia, S., LEAP+: Efficient security mechanisms for large-scale distributed sensor networks. ACM Tran. Sens. Netw. 2(4):500–528, November 2006.
Kuo, C., Luk, M., Negi, R., Perrig, A., Message-in-a-bottle: user-friendly and secure key deployment for sensor nodes. Proc. of the Fifth International Conference on Embedded Networked Sensor Systems (SenSys’07), ACM. Sydney, Australia, 233–246, 2007.
Simplício, M. A., Jr., Barreto, P. S. L. M., Margi, C. B., and Carvalho, T. C. M. B., A survey on key management mechanisms for distributed Wireless Sensor Networks. Comput. Netw. 54(15):2591–2612, 2010.
Chen, M., Gonzalez, S., Vasilakos, A., Cao, H., and Leung, V. M., Body Area Networks: A survey. Mobile Netw. Appl. 16(2):171–193, 2011.
Ullah, S., Higgins, H., Braem, B., Latre, B., Blondia, C., Moerman, I., Saleem, S., Rahman, Z., and Kwak, K., A comprehensive survey of Wireless Body Area Networks. J. Med. Syst. 36(3):1065–1094, 2012.
Latré, B., Braem, B., Moerman, I., Blondia, C., and Demeester, P., A survey on wireless body area networks. Wirel. Netw 17(1):1–18, 2011.
Li, M., Wenjing, L., and Kui, R., Data security and privacy in wireless body area networks. IEEE Wirel. Commun. 17(1):51–58, 2010.
Ameen, M., Liu, J., and Kwak, K., Security and privacy issues in wireless sensor networks for healthcare applications. J. Med. Syst. 36(1):93–101, 2012.
Irum, S., Ali, A., Khan, F. A., and Abbas, H., A hybrid security mechanism for intra-WBAN and inter-WBAN communications. Int. J. Distrib. Sens. Netw 2013:11, 2013. Article ID 842608.
Ali, A., and Khan, F. A., Energy-efficient cluster-based security mechanism for intra-WBAN and inter-WBAN communications for healthcare applications. EURASIP J. Wirel. Commun. Netw. 2013:216, 2013. doi:10.1186/1687-1499-2013-216.
Juels, A., and Wattenberg, M., A fuzzy commitment scheme. Proc. of the 6th ACM Conference on Computer and Communications Security (CCS’99), ACM, Singapore, 28–36, 1999.
Chunqiang, H., Xiuzhen, C., Fan, Z., Dengyuan, W., Xiaofeng, L., and Dechang, C., OPFKA: Secure and efficient ordered-physiological feature-based key agreement for wireless body area networks. Proc. of IEEE INFOCOM’13, Turin, Italy, pp. 2274–2282, 2013.
Venkatasubramanian, K. K., Banerjee, A., and Gupta, S. K. S., Plethysmogram-based secure inter-sensor communication in body area networks. Proc. of Military Communications Conference (MILCOM’08), IEEE, San Diego, CA, USA, 1–7, 2008.
Venkatasubramanian, K. K., Banerjee, A., and Gupta, S. K. S., PSKA: Usable and secure key agreement scheme for body area networks. IEEE Trans. Inf. Technol. Biomed. 14(1):60–68, 2010.
Venkatasubramanian, K. K., Banerjee, A., and Gupta, S. K. S., Green and sustainable cyber-physical security solutions for body area networks. Proc. of Sixth International Workshop on Wearable and Implantable Body Sensor Networks, IEEE, Berkeley, CA, USA, 240–245, 2009.
Juels, A. and Sudan, M., A fuzzy vault scheme. Proc. Of International Symposium on Information Theory (ISIT’02), IEEE, Lausanne, Switzerland, 2002.
Zhang, G.H., Poon, C.C.Y. and Zhang, Y.T., A fast key generation method based on dynamic biometrics to secure wireless body sensor networks for p-health. Proc. Annual International Conference of the Engineering in Medicine and Biology Society (EMBC), IEEE, Buenos Aires, Argentina, 2034–2036, 2010.
Fen, M., Lei, J.,Ye, L., and Yuan-Ting, Z., Biometrics based novel key distribution solution for body sensor networks. Proc. of Annual International Conference of the Engineering in Medicine and Biology Society (EMBC), IEEE, Minneapolis, MN, 2458–2461, 2009.
Shu-Di, B., Poon, C. C. Y., Yuan-Ting, Z., and Lian-feng, S., Using the timing information of heartbeats as an entity identifier to secure body sensor network. IEEE Trans. Inf. Technol. Biomed. 12(6):772–779, 2008.
Shu-Di, B., Lian-Feng, S., and Yuan-Ting, Z., A novel key distribution of body area networks for telemedicine. International Workshop on Biomedical Circuits and Systems, IEEE, Singapore, 1–17–20a, 2004.
Cherukuri, S., Venkatasubramanian, K.K., and Gupta, S.K.S., Biosec: A biometric based approach for securing communication in wireless networks of biosensors implanted in the human body. Proc. of International Conference on Parallel Processing Workshops, IEEE, Kaohsiung, Taiwan, 432–439, 2003.
Miao, F., Bao, S. D., and Li, Y., Biometric key distribution solution with energy distribution information of physiological signals for body sensor network security. IET Inf. Secur. 7(2):87–96, 2013.
Cun-Zhang, C., Chen-Guang, H., Shu-Di, B., and Ye, L., Improvement of fuzzy vault scheme for securing key distribution in body sensor network. Annual International Conference of the Engineering in Medicine and Biology Society (EMBC), IEEE, Boston, MA, USA, 3563–3567, 2011.
Fen, M., Shu-Di, B. and Ye, L., A modified fuzzy vault scheme for biometrics-based body sensor networks security. Proc. of Global Telecommunications Conference (GLOBECOM’10), IEEE, Miami, FL, USA, 1–5, 2010.
Jinyang, S., Kwok-Yan, L., Ming, G., Mingze, L., and Siu-Leung, C., Towards energy-efficient secure communications using biometric key distribution in wireless biomedical healthcare networks. Proc. of 2nd International Conference on Biomedical Engineering and Informatics (BMEI’09), IEEE, Tianjin, China, 1–5, 2009.
Bui, F.M., and Hatzinakos, D., Resource allocation strategies for secure and efficient communications in biometrics-based body sensor networks. Proc. Of Biometrics Symposium, IEEE, Baltimore, MD, USA, 1–6, 2007.
Zhaoyang, Z., Honggang, W., Vasilakos, A. V., and Hua, F., ECG-cryptography and authentication in body area networks. IEEE Trans. Inf. Technol. Biomed. 16(6):1070–1078, 2012.
Dodis, Y., Reyzin, L., and. Smith, A., Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. Advances in Cryptology—EUROCRYPT’04 Lecture Notes in Computer Science, 3027:523–540, 2004.
Honggang, W., Hua, F., Liudong, X., and Min, C., An integrated biometric-based security framework using wavelet-domain HMM in wireless body area networks (WBAN). Proc. of International Conference on Communications (ICC), IEEE, Kyoto, Japan, 1–5, 2011.
Venkatasubramanian, K.K., Banerjee, A., and Gupta, S.K.S., EKGbased key agreement in body sensor networks. Proc. of IEEE INFOCOM Workshops, IEEE, Phoenix, AZ, USA, 1–6, 2008.
Ali, A., Irum, S., Kausar, F., and Khan, F. A., A cluster-based key agreement scheme using keyed hashing for body area networks. Multimed, Tools Appl. 66(2):201–214, 2013.
Venkatasubramaniam, K. K., and Gupta, S. K. S., Physiological valuebased efficient usable security solutions for body sensor networks. ACM Trans. Sens. Netw. (TOSN) 6(4):60–68, 2010.
Ali, A., and Khan, F. A., An improved EKG-based key agreement scheme for body area networks. Proc. of 4th International Conference on Information Security and Assurance (ISA’10), Miyazaki, Japan. Commun. Comput. Inf. Sci. 76:298–308, June 2010.
Wei, W., Kun, H., Hempel, M., Dongming, P., Sharif, H., and Hsiao-Hwa, C., A stochastic biometric authentication scheme using uniformed GMM in wireless body area sensor networks. Proc. of 21st International Symposium on Personal Indoor and Mobile Radio Communications (PIMRC’10), IEEE, Instanbul, Turkey, 1620–1624, 2010.
Ali, A., and Khan, F. A., A broadcast-based key agreement scheme using set reconciliation for wireless body area networks. J. Med. Syst. 38(5):1–12, 2014.
Wu, Y., Sun, Y., Zhan, L., and Ji, Y., Low mismatch key agreement based on wavelet-transform trend and fuzzy vault in body area network. Int. J. Distrib. Sens. Netw. 2013:16, 2013. Article ID 912873.
Xin, H., Bangdao, C., Markham, A., Qinghua, W., Zheng, Y., and Roscoe, A. W., Human interactive secure key and identity exchange protocols in body sensor networks. Inf. Secur. IET 7(1):30–38, 2013.
Yi, R., Oleshchuk, V., Li, F.Y., and Sulistyo, S., FoSBaS: A bi-directional secrecy and collusion resilience key management scheme for BANs. Proc. of Wireless Communications and Networking Conference (WCNC’12), IEEE, Shanghai, China, 2841–2846, 2012.
Jingwei, L., Zonghua, Z., Rong, S., and Kyung Sup, K., An efficient certificateless remote anonymous authentication scheme for wireless body area networks. Proc. International Conference on Communications (ICC), IEEE, Ottawa, ON, Canada, 3404–3408, 2012.
Jin-Meng, H., A versatile suite of strong authenticated key agreement protocols for body area networks. Proc. of 8 th International Wireless Communications and Mobile Computing Conference (IWCMC’12), IEEE, Limassol, Cyprus, 683–688, 2012.
Drira, W., Renault, E., and Zeghlache, D., A hybrid authentication and key establishment scheme for WBAN. Proc. of 11th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom’12), IEEE, Liverpool, England, 78–83, 2012.
Hu, C., Zhang, N., Li, H., Cheng, X., and Liao, X., Body area network security: A fuzzy attribute-based signcryption scheme. J. Sel. Areas Commun. 31(9):37–46, 2013.
Barua, M., Alam, M.S., Xiaohui L., and Xuemin, S., Secure and quality of service assurance scheduling scheme for WBAN with application to eHealth. Proc. of Wireless Communications and Networking Conference (WCNC’11), IEEE, Cancun, Mexico, 1102–1106, 2011.
Möller, S., Newe, T., and Lochmann, S., Prototype of a secure wireless patient monitoring system for the medical community. Sensors Actuators A Phys. 173(1):55–65, 2012.
Yao, L., Ali, S.T., Sivaraman, V., and Ostry, D., Improving secret key generation performance for on-body devices. Proc. of 6th International Conference on Body Area Networks (BodyNets '11), ICST, Beijing, China, 19–22, 2011.
Shen, J., Moh, S., and Chung, I., A novel key management protocol in body area networks. Proc. of the Seventh International Conference on Networking and Services (ICNS’11), IARIA, Venice, Italy, 246–251, 2011.
Li, M., Shucheng, Y., Wenjing, L., and Kui, R., Group device pairing based secure sensor association and key management for body area networks. Proc. of INFOCOM’10, IEEE, San Diego, CA, USA, 1–9, 2010.
Kanjee, M.R., Divi, K., and Hong, L., A two-tiered authentication and encryption scheme in secure healthcare sensor networks. Proc. of Sixth International Conference on Information Assurance and Security (IAS), IEEE, Atlanta, GA, USA, 271–276, 2010.
Morchon, O.G., and Baldus, H., Efficient distributed security for wireless medical sensor networks. Proc. of International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), IEEE, Sydney, Australia, 249–254, 2008.
Morchon, O.G., Baldus, H., and Sanchez, D.S., Resource-efficient security for medical body sensor networks. Proc. of International Workshop on Wearable and Implantable Body Sensor Networks (BSN’06), IEEE, Cambridge, MA, USA, 80–83, 2006.
Sanchez, D.S., and Baldus, H., A deterministic pairwise key pre-distribution scheme for mobile sensor networks. Proc. of First International Conference on Security and Privacy for Emerging Areas in Communications Networks (SecureComm), IEEE, Athens, Greece, 277–288, 2005.
Huang, C., Lee, H., and Lee, D., A privacy-strengthened scheme for E-Healthcare monitoring system. J. Med. Syst. 36(5):2959–2971, 2012.
Selimis, G., Huang, L., Massé, F., Tsekoura, I., Ashouei, M., Catthoor, F., Huisken, J., Stuyt, J., Dolmans, G., Penders, J., and De Groot, H., A lightweight security scheme for wireless body area networks: design, energy evaluation and proposed microprocessor design. J. Med. Syst. 35(5):1289–1298, 2011.
Zhao, Z., An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 38(2):1–7, 2014.
Daojing, H., Chun, C., Chan, S., Jiajun, B., and Pingxin, Z., Secure and lightweight network admission and transmission protocol for body sensor networks. IEEE J. Biomed. Health Inf. 17(3):664–674, 2013.
Mana, M., Feham, M., and Bensaber, B. A., Trust key management scheme for wireless body area networks. Int. J. Netw. Secur. 12(2):75–83, 2011.
Fengyuan, X., Zhengrui, Q., Tan, C.C., Baosheng, W., and Qun, L., IMDGuard: Securing implantable medical devices with the external wearable guardian. Proc. of INFOCOM’11, IEEE, Shanghai, China, 1862–1870, 2011.
Yao, L., Liu, B., Wu, G., Yao, K., and Wang, J., A biometric key establishment protocol for body area networks. Int. J. Distrib. Sens. Netw. 2011:10, 2011. Article ID 282986.
Raazi, S.M.K.R., Sungyoung, L., Young-Koo, L., and Heejo, L., BARI: A distributed key management approach for wireless body area networks. Proc. of International Conference on Computational Intelligence and Security (CIS ’09), IEEE, Beijing, China, 324–329, 2009.
Raazi, S. M. K. R., Heejo, L., Sungyoung, L., and Young-Koo, L., BARI+: A biometric based distributed key management approach for wireless body area networks. Sensors 10(4):3911–3933, 2010.
Mana, M., Feham, M., and Bensaber, B. A., SEKEBAN (Secure and efficient key exchange for wireless body area network). Int. J. Adv. Sci. Technol. 12:45–60, 2009.
Zhang, G.H., Poon, C.C.Y., Ye, L. and Zhang, Y.T. A biometric method to secure telemedicine systems. Proc. of Annual International Conference of the Engineering in Medicine and Biology Society (EMBC), Minneapolis, MN, USA, IEEE, 701–704, 2009.
Shu-Di, B., and Yuan-Ting, Z., A design proposal of security architecture for medical body sensor networks. Proc. of International Workshop on Wearable and Implantable Body Sensor Networks (BSN’06), IEEE, Cambridge, MA, USA, 67–90, 2006.
Acknowledgements
The authors would like to extend their sincere appreciation to the Deanship of Scientific Research at King Saud University for its funding of this research through the Research Group Project no. RGP-VPP-214. The authors would also like to thank the Higher Education Commission (HEC), Pakistan, for its support through the indigenous PhD fellowship program.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Patient Facing Systems
Rights and permissions
About this article
Cite this article
Ali, A., Khan, F.A. Key Agreement Schemes in Wireless Body Area Networks: Taxonomy and State-of-the-Art. J Med Syst 39, 115 (2015). https://doi.org/10.1007/s10916-015-0272-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-015-0272-9