Abstract
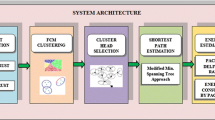
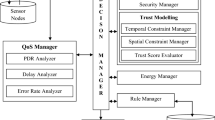
Secure and trustable routing is one of the remarkable challenges in wireless sensor networks (WSNs). In this paper, we proposed a secure, trustable and energy-efficient routing method for WSNs. The proposed scheme uses Fuzzy logic to obtain the trust values of the routes. Then, the shortest route from the source to the destination was selected by considering trust and security. The proposed method uses the multidimensional scaling-map (MDS-MAP) optimal routing approach and measures the trust model via fuzzy logic. The proposed method was compared with Trust and Centrality degree Based Access Control (TC-BAC) and Trust-Aware Routing Framework (TARF) protocols. Through simulation experiment result, we show that the proposed scheme performs better than TC-BAC and TARF methods in terms of average packet delivery rate, average end-to-end delay and consumption energy.










Similar content being viewed by others
References
Nikokheslat, H. D., & Ghaffari, A. (2017). Protocol for controlling congestion in wireless sensor networks. Wireless Personal Communications, 95(3), 3233–3251.
Ghaffari, A. (2015). Congestion control mechanisms in wireless sensor networks: A survey. Journal of Network and Computer Applications, 52, 101–115.
Wu, F., Xu, L., Kumari, S., & Li, X. (2017). A new and secure authentication scheme for wireless sensor networks with formal proof. Peer-to-Peer Networking and Applications, 10(1), 16–30.
Zhou, Y., Fang, Y., & Zhang, Y. (2008). Securing wireless sensor networks: A survey. IEEE Communications Surveys Tutorials&, 10(3), 6–28.
Djenouri, D., Khelladi, L., & Badache, N. (2005). A survey of security issues in mobile ad hoc networks. IEEE Communications Surveys, 7(4), 2–28.
Ahmed, A., Bakar, K. A., Channa, M. I., Khan, A. W., & Haseeb, K. (2017). Energy-aware and secure routing with trust for disaster response wireless sensor network. Peer-to-Peer Networking and Applications, 10(1), 216–237.
Jin, X., Liang, J., Tong, W., Lu, L., & Li, Z. (2017). Multi-agent trust-based intrusion detection scheme for wireless sensor networks. Computers and Electrical Engineering, 59, 262–273.
Zhan, G., Shi, W., & Deng, J. (2012). Design and implementation of TARF: A trust-aware routing framework for WSNs. IEEE Transactions on Dependable and Secure Computing, 9(2), 184–197.
Pirzada, A. A., McDonald, C., & Datta, A. (2006). Performance comparison of trust-based reactive routing protocols. IEEE Transactions on Mobile Computing, 5(6), 695–710.
Li, X., Jia, Z., Zhang, P., Zhang, R., & Wang, H. (2010). Trust-based on-demand multipath routing in mobile ad hoc networks. IET Information Security, 4(4), 212–232.
Cho, J.-H., Swami, A., & Chen, I.-R. (2011). A survey on trust management for mobile ad hoc networks. IEEE Communications Surveys and Tutorials, 13(4), 562–583.
Duan, J., Gao, D., Heng Foh, C., & Zhang, H. (2013). TC-BAC A trust and centrality degree based access control model in wireless sensor networks. Ad Hoc Networks, 11(8), 2675–2692.
Mitchel, R., & Mitchel, I.-R. (2014). A survey of intrusion detection in wireless network applications. Computer Communications, 42, 1–23.
Shin, S., Kwon, T., Jo, G.-Y., Park, Y., & Rhy, H. (2010). An experimental study of hierarchical intrusion detection for wireless industrial sensor networks. IEEE Transactions on Industrial Informatics, 6(4), 744–757.
Ganeriwal, S., & Srivastava, M. (2004). Reputation-based framework for high integrity sensor networks. In Proceedings of the ACM workshop on security of ad hoc and sensor networks (pp. 66–77).
Han, G., Jiang, J., Shu, L., Niu, J., & Chao, H. (2013). Management and applications of trust in wireless sensor networks: A survey. Journal of Computer and System Sciences, 8(3), 602–617.
Kim, T. K., & Seo, H. S. (2008). A trust model using fuzzy logic in wireless sensor network. Proceedings of World Academy of Science Engineering and Technology, 18, 63–66.
Yao, Z., Kim, D., & Doh, Y. (2008). PLUS: Parameterized and Localized trust management Scheme for sensor networks security. In IEEE international conference on mobile ad-hoc and sensor systems (pp. 437–446).
Michiardi, P., & Molva, R. (2002). CORE: A collaborative reputation mechanism to enforce node cooperation in mobile ad-hoc networks. In The IFIP TC6/TC11 sixth joint working conference on communications and multimedia security: Advanced communications and multimedia security Portoroz, Slovenia (pp. 107–121).
Boukerch, A., Xu, L., & El-Khatib, K. (2007). Trust-based security for wireless ad hoc and sensor networks. Computer Communications, 30(11–12), 2413–2427.
Mishra, A., Sudan, K., & Soliman, H. (2010). Detecting border intrusion using wireless sensor network and artificial neural network. In 2010 6th IEEE international conference on distributed computing in sensor systems workshops (DCOSSW) (pp. 1–6).
Khanna, R., Liu, H., & Chen, H.-H. (2009). Reduced complexity intrusion detection in sensor networks using genetic algorithm. In IEEE ICC.
Xiong, L., & Liu, L. (2004). Peer trust: supporting reputation-based trust in peer-to-peer communities. IEEE Transactions on Knowledge and Data Engineering, 16(7), 843–857.
Zapata, M. G., & Asokan, N. (2002). Securing ad hoc routing protocols. In Proceedings of the 1st ACM workshop on wireless security (pp. 1–10).
Cerri, D., & Ghioni, A. (2008). Securing AODV: The A-SAODV secure routing prototype. IEEE Communications Magazine, 46(2), 120–125.
Umar, I. A., Hanapi, Z. M., Sali, A., & Zulkarnain, Z. A. (2017). TruFiX: A configurable trust-based cross-layer protocol for wireless sensor networks. IEEE Access, 5, 2550–2562.
Ahmed, A., Bakar, K. A., Channa, M. I., Khan, A. W., & Haseeb, K. (2017). Energy-aware and secure routing with trust for disaster response wireless sensor network. Peer-to-Peer Networking and Applications, 10(1), 216–237.
Vasserman, E. Y., & Hopper, N. J. (2013). Vampire attacks: Draining life from wireless ad hoc sensor networks. IEEE Transactions on Mobile Computing, 12(2), 318–332.
Daojing, H., Chun, C., Chan, S., Bu, J., & Vasilakos, A. V. (2012). ReTrust: Attack-resistant and lightweight trust management for medical sensor networks. IEEE Transactions on Information Technology in Biomedicine, 16, 623–632.
Liu, Y., Dong, M., Ota, K., & Liu, A. (2016). Active Trust: secure and trustable routing in wireless sensor networks. IEEE Transactions on Information Forensics and Security, 11(9), 2013–2027.
Yu, Y., Li, K., Zhou, W., & Li, P. (2012). Trust mechanisms in wireless sensor networks: Attack analysis and countermeasures. Journal of Network and Computer Applications, 35(3), 867–880.
Ayday, E., & Fekri, F. (2012). An iterative algorithm for trust management and adversary detection for delay-tolerant networks. IEEE Transactions on Mobile Computing, 11(9), 1514–1531.
Kamvar, S., Schlosser, M., & Garcia-Molina, H. (2003). The EigenTrust algorithm for reputation management in P2P networks. In Proceedings of the international world wide web networks, Proceedings of the international world wide web conference (pp. 173–186).
Zhoh, R., & Hwang, K. (2007). PowerTrust: A robust and scalable reputation system for trusted peer to peer computing. IEEE Transaction on Parallel and Distributed Systems, 18(4), 460–473.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Beheshtiasl, A., Ghaffari, A. Secure and Trust-Aware Routing Scheme in Wireless Sensor Networks. Wireless Pers Commun 107, 1799–1814 (2019). https://doi.org/10.1007/s11277-019-06357-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06357-3